New Case Study: SYMBITS - Managed Services Provider

RiskRecon provides cybersecurity capabilities way beyond ratings. It’s the only solution that automatically provides risk prioritization and continuous
monitoring.
Complete
third-party
security reports
RiskRecon automatically collects security information about vendors, partners and your own enterprise. It helps you understand how well each organization manages their digital footprint and swiftly take remediate open issues.

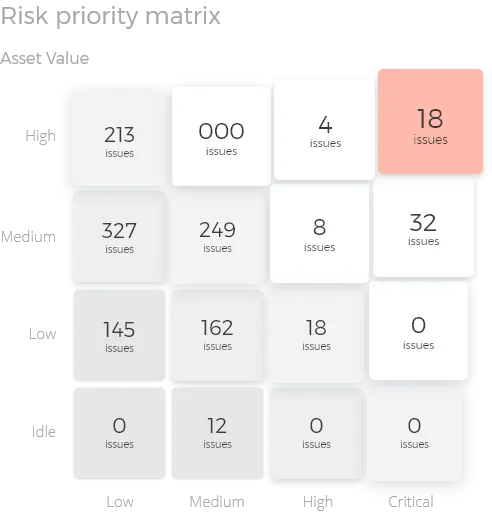
Risk-prioritized
ratings
It provides risk-prioritized ratingsallowing you to address the most important items first, based on issue severity and the system value at risk.
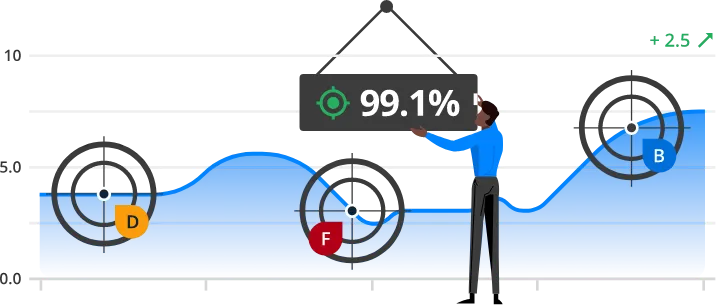
Data Accuracy
The platform data is certified to be 99.1% accurate. These data combine patent-pending machine learning automation and human analyst quality control that form the foundation for accurate data necessary to prioritize risk.
Automated Action Plans Based on Your Risk Policy
RiskRecon automatically produces action plans to highlight only issues that exceed your company’s risk policy threshold.
Full Data Access and Transparency
The assessment details are all visible to you and your vendors at no additional fee. Action requires accuracy and transparency. RiskRecon provides you both.

Streamline your third-party risk management process.
Small businesses deserve big, secure solutions.
See everything Haven can do for your business.
Single Source
Companies rated a “C” have a 3x higher frequency of breaches than those rated “A”.

Based on a sample of 46,000 companies tracked by RiskRecon
67%
Increase in security breaches
in the last five years.
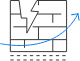
Source: Accenture. Ninth Annual Cost of Cybercrime Study. 2019
+50%
Of all companies have experienced a third-party breach yet only 16% are able to mitigate those risks.

Source: Ponemon Institute. Data Risk in the Third-Party Ecosystem. 2018
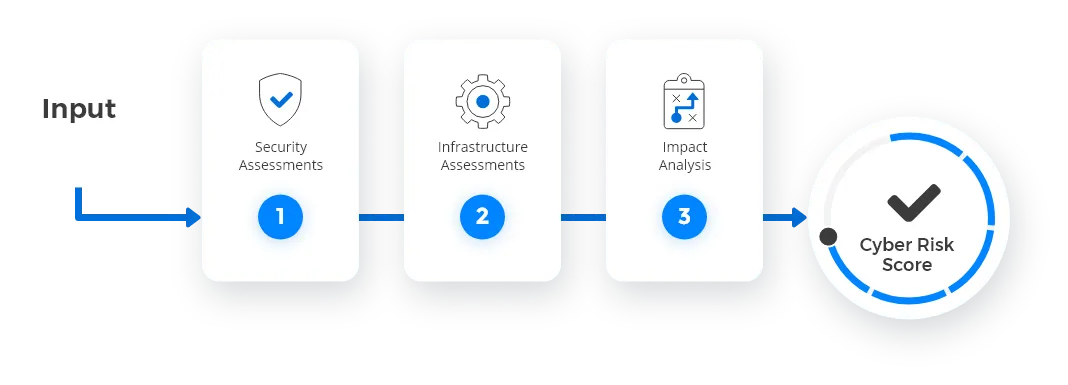
How is the RiskRecon cyber risk
Score determined?
The cyber risk score is determined by evaluating over 36 criteria across 9 security domains. The
impact of all vulnerabilities is analyzed to produce a cyber risk score.